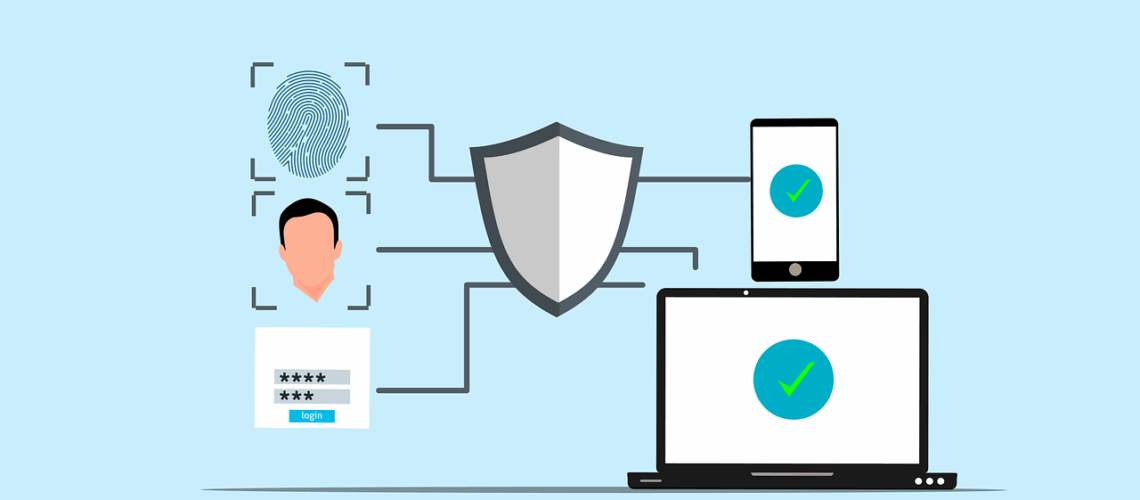
Have you ever wondered how vulnerable your business is to cyberattacks? According to recent reports, nearly 43% of cyberattacks target small businesses, often exploiting weak security measures. One of the most overlooked yet highly effective ways to protect your company is through Multi-Factor Authentication (MFA). This extra layer of security makes it significantly harder for hackers to gain access, even if they have your password. This article explains how to implement Multi-Factor Authentication for your small business. With this knowledge, you’ll be able to take a crucial step in safeguarding your data and ensuring stronger protection against potential cyber threats.Why is Multi-Factor Authentication Crucial for Small Businesses?Before diving into the implementation process, let’s take a step back and understand why Multi-Factor Authentication (MFA) is so essential. Small businesses, despite their size, are not immune to cyberattacks. In fact, they’re increasingly becoming a target for hackers. The reality is that a single compromised